Chen Shiri is a cyber security researcher, hacker, known for his research on low-level security and isolation mechanisms, working with leading security firms, government organizations and Fortune 500 companies.
His research has revealed significant flaws in widely used services and prominent vendors, impacting millions of users worldwide and shaping security best practices across the industry. He has published work demonstrating early examples of weaknesses in microservices, container-based web applications, and products like Google Colab and Cloud Shell, in addition to a chain attack in AWS Kubernetes services.
Frequently cited by major news outlets, his research has influenced both academia and industry, driving meaningful security improvements.
He is also a seasoned public speaker, presenting at top security conferences and sharing deep technical insights on exploitation techniques, mitigations, and emerging threats.
Security Researcher, Expert – Accenture 2020 – Current (2025)
Maglan- Cyber Warfare and IT Security Research Labs

Outside of my research and business, enjoy from:
– Practicing powerlifting and jiu-jitsu
– Playing guitar
Media

Newspaper Article About a Patent Invention
An interview with a leading news paper article about a development of a patent for visually impaired people

Presenting at Hackeriot Cyber Summit
Volunteer lecturer at “Hackeriot Summit”
A conference to promote woman in cyber

Talk about a New Vulnerability for Escaping Docker Containers Talk
I was honored to present about attacking cloud container orchestrations

Lecturing to Israeli Air Force (IDF)
I had the honor of sharing my knowledge about advanced microservices to the Israeli Air Force (IDF)
New Posts
From Stage to Screen: Reflections from BSidesNoVA and the Mr. Robot 10-Year Anniversary
Last week, I had the privilege of speaking at Security...
Read MoreMore Than a Talk: What I Learned at Hacktivity
Two weeks ago, I had the honor of presenting my...
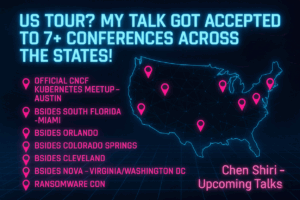
Read MoreUS Tour? My Talk Was Accepted to 7+ Cons Across the States!
What started as a single CFP submission turned into something...
Read MoreMy Talk Got Accepted for the Official CNCF Kubernetes Conference in Austin, Texas
This morning started with one of those emails you never...
Read MoreResearch & Publications
Hacking Azure Key Vault- Exploring Authentication Problem
Summary: The article focuses on intricacies of managed identity authentication in Azure Key Vault and it’s critical security issue. I describe exploitation of the issue in environments where this feature is used, could allow attackers inside a container to get the secrets of all containers on the node. It examines the problem of secret management in relation to application security and evaluates Azure Key Vault’s solution. With practical implementation insights and an in-depth analysis of the attack vector, the research uncovers how it impact cloud environments and how to execute the attack.
AWS Elastic Kubernetes Service (EKS) Chain Attack
Summary: In this research article, I present a new attack methodology targeting Elastic Kubernetes Service (EKS) on AWS. By uncovering two zero-day vulnerabilities, I demonstrate how attackers can exploit the weaknesses in EKS’s pod isolation mechanism. This research highlights the critical security risks and implications, including unauthorized access to customer data, non-compliance with regulations, and potential financial and reputational damage. The article provides detailed insights into the attack techniques and offers recommendations for mitigating these vulnerabilities to safeguard EKS environments.
Vulnerability in Google Colab: Access to Host VMs via Container Escapes
Research- Medium
Summary: The research explores a vulnerability discovered in Google Colab, a popular online platform for coding and data analysis. The vulnerability involves access to host virtual machines (VMs) through container escapes. The author highlights the significance of this vulnerability by demonstrating how an attacker with access to a Colab notebook could exploit it to gain unauthorized access to the underlying infrastructure, potentially compromising sensitive data or launching malicious activities. The article offers a detailed analysis of the vulnerability, including the underlying mechanisms and consequences, emphasizing the importance of addressing such security flaws to ensure the continued safety and integrity of cloud-based platforms.
Taking over “Google Cloud Shell” by utilizing capabilities and Kubelet
Summary: Research conducted by Chen Shiri reveals critical vulnerabilities in Google Cloud Shell, a free interactive shell used for running projects and testing online. The study identified an attack vector that could expose secrets and container data, including tokens, and allow malicious actors to read and modify data stored and accessible from other containers and services. Shiri successfully broke out of the container and gained read/write access to Google’s infrastructure, accessing all containers on the node, including critical files and instance information, and gaining root access to the node. The vulnerabilities exposed in the study could potentially compromise the authorization, credentials, tokens, images, and container registry of Google’s shell mechanism, and provide access to different shell sessions, instance information, and configuration and data for the containers running on the node.